Disaster recovery planning does not usually fail because the tools are weak. It fails because the tools are misunderstood, misused or left running on assumptions that no longer hold. Most organisations only realise this after something breaks. By then, the conversation is no longer about resilience. It is about blame, delay and cost.
DRP tools sit in an awkward space. They are essential, but rarely loved. They do not stop attacks. They do not block ransomware. They exist for the uncomfortable moment after prevention has failed and availability suddenly matters more than elegance.
That is where their real value sits.
What DRP Tools are Really Doing Behind the Scenes
It is tempting to describe DRP tools in neat functional buckets. Backup. Replication. Orchestration. That framing looks tidy on a slide, but it misses how these tools behave in the real world.
Most modern DRP tools are less about technology and more about discipline. They enforce timing, dependencies and order when human judgement is at its worst. Under pressure, teams forget runbooks. They skip steps. They restore the wrong system first.
A DRP tool does not panic. It executes what was defined weeks or months earlier. That is both its strength and its risk.
There exists environments where recovery plans are present only inside the tool, never questioned after the first deployment. When infrastructure drifts, the DRP configuration quietly stayed the same. On paper, recovery time objectives looked healthy. In practice, they were fiction.
Why DRP Tools Often Disappoint During Incidents
When recovery fails, the tool usually takes the blame. That reaction is understandable but often misplaced.
Three patterns show up repeatedly.
First, DRP tools are implemented too late in the lifecycle. They are bolted onto complex estates that were never designed for clean recovery. Flat networks, hard-coded dependencies, legacy authentication flows. The tool can only work with what it sees.
Second, testing is shallow. Snapshot restores are tested. Full-service recovery is not. Teams prove that data can come back, but not that the business can operate. DRP tools faithfully report success while users still cannot log in.
Third, ownership is unclear. Is disaster recovery an infrastructure problem, a security problem or an application problem? When everyone owns it, no one truly does. The tool sits in the middle, configured by one team, depended on by many.
Where DRP Tools Quietly Earn Their Keep
Despite the criticism, DRP tools matter. When used well, they reduce chaos in ways that are hard to quantify until something goes wrong.
- They enforce recovery order when applications have hidden dependencies.
- They provide repeatability when staff availability is reduced.
- They give executives something solid to lean on when decisions need to be made quickly.
- Most importantly, they create a forcing function for uncomfortable conversations. Recovery time objectives stop being theoretical when a tool refuses to meet them without architectural change.
That tension is healthy.
A Simple Way to Visualise a DRP Workflow
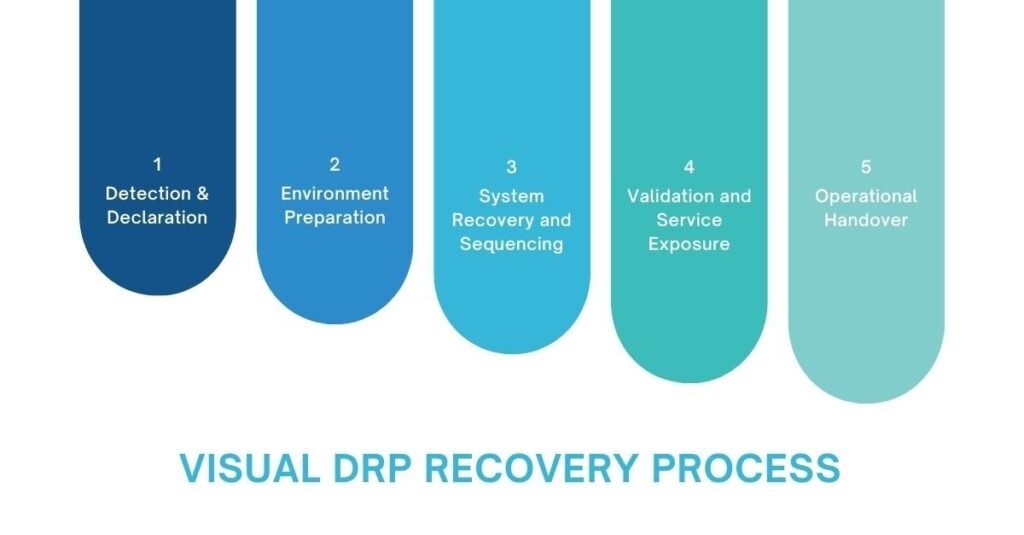
A DRP tool is not a single action. It is a chain, and the chain is only as strong as its weakest link.
A simplified recovery flow often looks like this:
- Detection & Declaration
An incident is recognised as a disaster, not just an outage. This decision still tends to be human, even in mature environments.
- Environment Preparation
Networks, identity services, and access controls are brought into a known state before any data is touched.
- System Recovery and Sequencing
Core services are restored in a defined order. Databases before applications. Identity before users.
- Validation and Service Exposure
Recovery is not complete when systems power on. It is complete when services function as expected.
- Operational Handover
Responsibility moves back to business and IT operations, often while investigation continues in parallel.
Good DRP tools make this flow visible. Bad ones hide it behind green ticks.
DRP Tools and Ransomware Realities
Ransomware has changed how DRP tools are evaluated. Recovery is no longer just about speed. It is about safety.
Clean recovery points matter more than recent ones. Isolation matters more than convenience. Tools that cannot validate integrity or enforce separation quickly become liabilities.
Modern DRP tooling must integrate with security controls, not just sit beside them. Otherwise, recovery becomes reinfection at scale.
Choosing DRP Tools Without Chasing Features
Feature lists are rarely the right place to start. Most organisations will never use half of what they buy.
More useful questions sound less technical.
- Can this tool reflect our actual application dependencies, not just what the hypervisor sees?
- Can we test recovery without disrupting production teams every time?
- Does this tool force us to document assumptions we have been avoiding?
If the answer to those questions is unclear, the tool will not save you when it matters.
Conclusion
DRP tools are not silver bullets. They are mirrors. They reflect how well an organisation understands its own environment, its priorities and its tolerance for disruption.
When they are implemented thoughtfully, they reduce uncertainty at the worst possible moment. When they are treated as compliance artefacts, they offer comfort without capability.
This is where experienced support makes a difference. CyberNX is a reliable cybersecurity firm that provides comprehensive disaster recovery solutions from initial assessment and planning to implementation, continuous management, and 24/7 monitoring. Their expert team helps deploy effective disaster recovery strategies, maximizing resilience and ROI.
The real test of DRP tools is not how they perform in a demo. It is how quietly they work when everything else is noisy.

